NFT Trader is suspected to have been breached after several non-fungible tokens (NFTs) were mistakenly transferred.
According to an X-post by Chinese crypto news reporter Colin Wu, the NFTs were transferred to the address 0x909F2159780e64143CF08f32dBBF56Ed19478fda.
RED ALERT
If you have ever used NFT Trader in the past, please withdraw approval from the contract as soon as possible (0x13d8faF4A690f5AE52E2D2C52938d1167057B9af)
So far, 37 BAYC and 13 MAYC have already been transported to this address https://t.co/KBdpkb8woX
— dingaling (@dingalingts) December 16, 2023
Wu provided an update on the address holder’s on-chain message, denying that they had hacked the P2P trading platform and claiming that they had rescued the NFTs to return them.
The holder, who identified herself as a female ‘scavenger’, revealed the real hacker’s address as 0x3dc115307c7b79e9ff0afe4c1a0796c22e366a47b47ed2d82194bcd59bb4bd46
0x90…8fda sent a message to the chain denying that he was a hacker. He said he rescued these NFT assets and would return them, but demanded that the original holders pay him a 10% premium; and the real hacker was 0x3dc. ..bd46. https://t.co/3cXW7ibmcA
— Wu Blockchain (@WuBlockchain) December 16, 2023
NFT Trader also announced that it has suffered an attack on legacy smart contracts on X (formerly Twitter), asking users to remove delegations via Revoke.cash to the following addresses:
- 0xc310e760778ecbca4c65b6c559874757a4c4ece0
- 0x13d8faF4A690f5AE52E2D2C52938d1167057B9af
The P2P trading platform is relatively unknown to most NFT traders. the website states that the CEO is John Pak, who works with co-founders Mattia Migliore and an individual who goes by the pseudonym ‘Bruckzr’.
An attack has been made on old smart contracts. Remove the delegation via https://t.co/zEMgkS96nP to the following addresses:
-0xc310e760778ecbca4c65b6c559874757a4c4ece0
-0x13d8faF4A690f5AE52E2D2C52938d1167057B9af— NFT Trader (@NftTrader) December 16, 2023
On They identified all stolen digital assets, which amounted to more than $2 million, including 37 BAYC, 13 MAYC, 4 World of Women and 6 VeeFriends.
You might also like: US court sides with Yuga Labs and agrees that RC BAYC are copycats
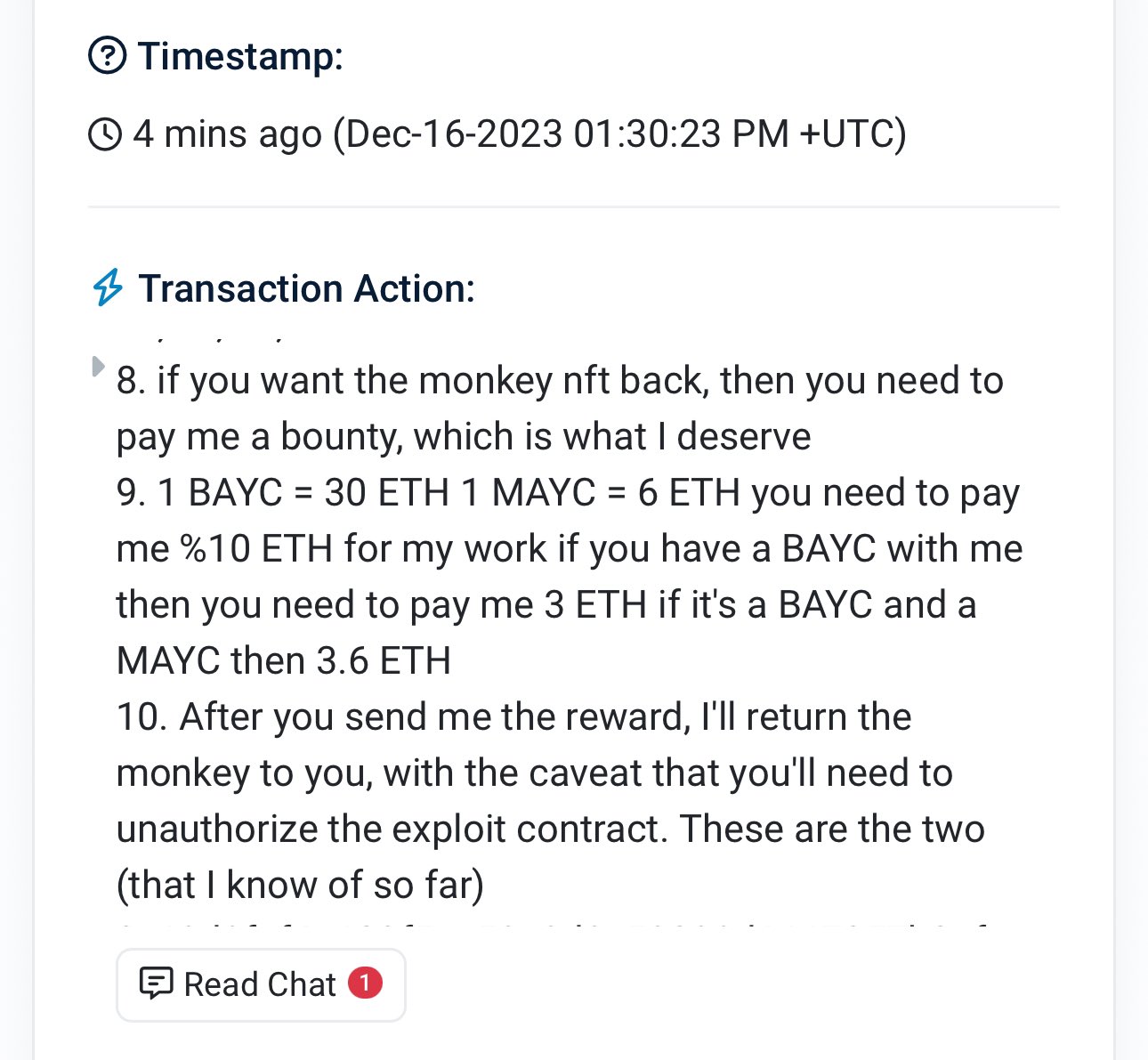
To get the hacker to return the NFTs, they sent a series of demands via their on-chain message, insisting that owners should pay them a bounty because “this is what they deserve”, asking for 10% of the values the NFTs for their “work”. ”
Don’t send ETH blindly‘
The crypto community is skeptical about the requirements. Market analysts like ZachXBT warn traders not to “blindly send their ETH.”
ZachXBT exchanged a few words with the exploiter and questioned the integrity of their word to return the assets.
The analyst believed that if they wanted to return the stolen assets, they would have to consider placing the Apes on the original wallet address or using an intermediary for the process.
Amazing things are happening for the Monkey NFT people
NFT Trader operator and ZachXBT exchange words pic.twitter.com/FAL0GgnvAt
— Davis
(@basedkarbon) December 16, 2023
Esports platform Kungama founder Michael Padilla, known as TFG, was one of the victims of the NFT Trade exploit.
TFG went to “
TFG acknowledged that it had not taken the necessary steps to protect its assets from the exploit, including revoking permissions for Etherscan.
I just ran out of my two favorite NFTs @BoredApeYC
Was empty because I used NFTtrader as a trading platform 1.5 years ago.
I assumed I wasn’t at risk because I removed the site as a connected site, but those aren’t the full steps. Must be withdrawn on etherscan
GG
pic.twitter.com/6MbK7Kwgp3
— TFG (@TFGmykL) December 16, 2023
According to the founder of Eden Block VC, which handles Lior.Eth on
An
They shared a JavaScript report of NFTTrader’s exploited smart contract, showing how everyone was helpless in pausing the contract because the platform’s team did not make the _pause function publicly visible.
– NFTTrader is being hacked
– the contract is pauseable, so they can pause if they are hacked
– the team cannot pause the contract because they forgot to make the _pause function visible to the publicthis is peak degeneration pic.twitter.com/Q2SvTXcSEJ
— @bytes032.xyz (@bytes032) December 16, 2023
The _pause function is used in a smart contract to stop all activities if something goes wrong. If the _pause function is not public, only the original creator can stop the contract and prevent further loss of funds.
However, if the original creator is unaware of the problem or is unavailable at the time, the hacker may be able to drain all the funds before anyone can stop it.
Nevertheless, light could shine between the dark clouds that the victims of the NFT Trader hack see, as BAYC founder Greg Solano has offered to pay 10% of the premium the exploiter has asked for to ensure that the NFTs be returned to their rightful owners. owners.
And if the information below is real, I will gladly stake the ETH to return these 50 monkeys to their rightful owners. https://t.co/7jBwQHQRCj
— Garga.eth (Greg Solano) (@CryptoGarga) December 16, 2023
Hacker returns one NFT without bounty
In a notable twist, the exploiter has willingly returned a World of Women (WOW) NFT at no cost, according to data from Etherscan. After returning the stolen WOW NFT, the hacker also returned a BAYC and a VFT to the rightful owners, without further payment notice.
Two more monkeys sent home by the @NftTrader operator. pic.twitter.com/M5GdhEoHUl
— Xeer (@Xeer) December 16, 2023
This unexpected twist has added a sense of unpredictability to the ongoing story, leaving the community both puzzled and unsure of the hacker’s motives.
Read more: BAYC NFT floor price drops 90% from $600,000 in 18 months


