Publication: The opinions and opinions expressed here are exclusively to the author and do not represent the views and opinions of the editorial editorial of crypto.news.
While the scandal continues to unfold and experts are investigating how serious top officials have affected American national security in that signal chat leak and has embarrassed themselves through controversial post-declarations I will look at a certain episode of the story.
Maybe you also like it: Since AI History rewrites, Blockchain Technology is a line of defense | Opinion
In the beginning, the White House denied that the chat once existed. But when it became clear that there was too much evidence to refute, they shifted tactics and denied that the chat once contained classified information about the meaning of national security. And indeed, what proof can journalist Jeffrey Goldberg be present after leaving that chat? Moreover, after a period of time, the chat was set to self -destructive messages. So imagine a hearing for the court where the parties are obliged to present evidence, and the only available evidence consists of screenshots – in other words, virtually nothing, because such evidence is almost impossible to verify.
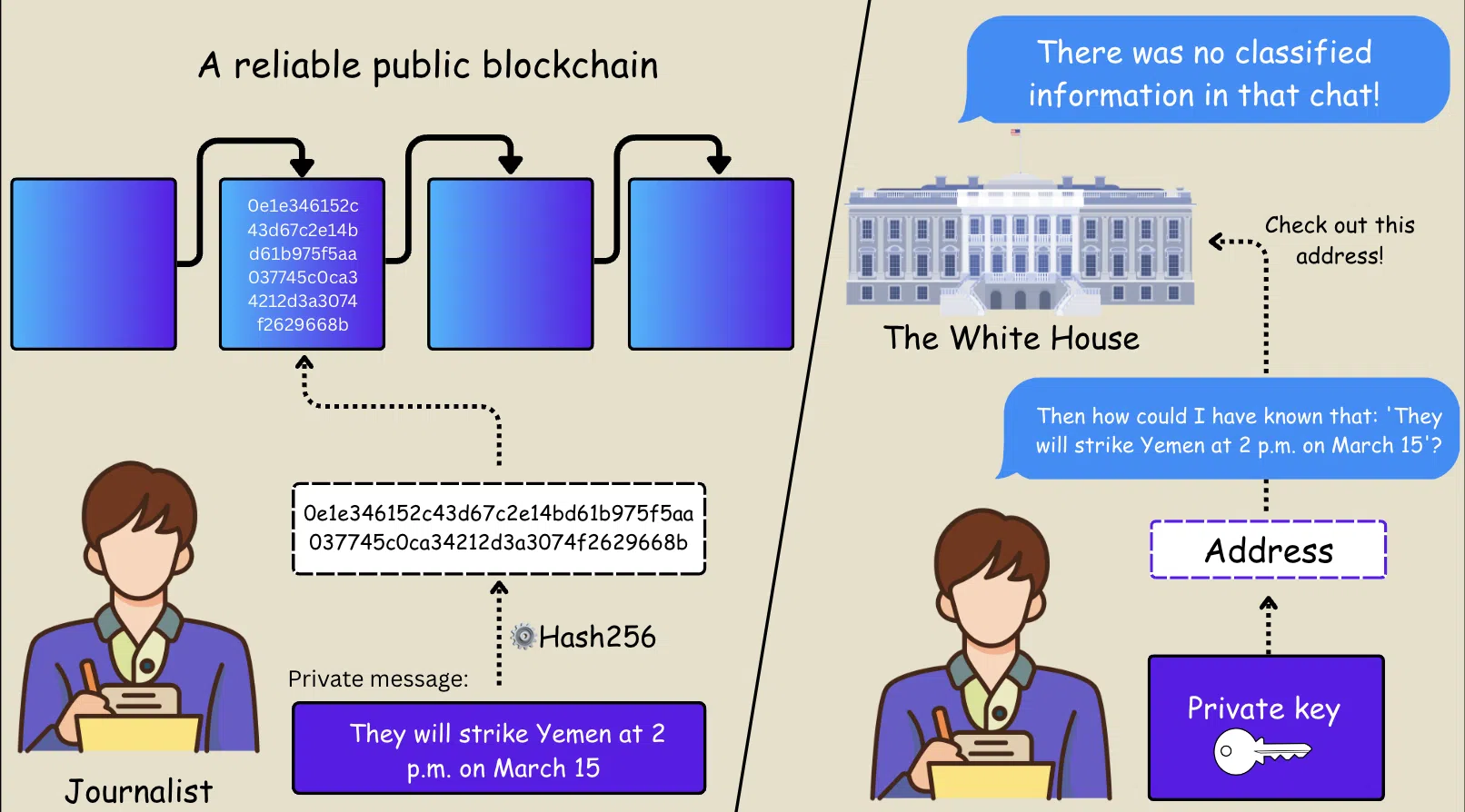
The answer is fairly simple – if the journalist had taken care of such proof. He could prove that he had access to sensitive information at a time when he should not have done that by publishing cryptographic hash amounts of that information. If he hadn’t been in the chat, he would not have known when and where they were planning to beat Yemen, who was the target, and so on. Certain details can become public later, but not when the chat took place – correct?
The solution lies in a cryptographic method that is known as proof of existence without disclosure. It includes two basic elements: cryptographic hashes and reliable time stamps. This can be done manually on blockchain and the process is known-or through various applications and services that offer-based recovery-based recovery.
This is how it works: you write a message (for example by copying and sticking from the chat), generates a hash sum of the message, publish it on a blockchain and save the private key for the address used to publish it. You later need this private key to prove that it was your address (that is, you personally) who published the hash, and therefore that you were then acquainted with the original message. An account on social media can also be a similar position, but remember that social platforms are centralized systems – fillable and, unlike block chains, not unchangeable.
So there it is – a note for all journalists who have to prove the existence of a fact one day without revealing its content.
Process diagram: proof of existence with blockchain | Source: Thanks to the author
This process creates an unmistakable, time stamp that confirms that there was a specific original message and was known to the publisher when the blockchain transaction was confirmed – all without revealing the content until the journalist chooses it.
Read more: Beyond Consensus: Transaction Privacy is Blockchain’s next security limit | Opinion

