The storage and secure management of data and passwords is one of the most important aspects in the crypto and blockchain world, and more generally in all online environments.
Encryption, intense as the art of ‘hidden writings’ that can convert plain text into cipher text and vice versa, comes to our rescue and makes it difficult for hackers to allow unauthorized access to certain networks and transactions.
Let’s take a look at the different methods by which encryption can protect valuable information and secure passwords.
Symmetric and asymmetric password encryption in the crypto sector
When talking about password security in cryptography, two encryption methods are commonly referred to: symmetric and asymmetric.
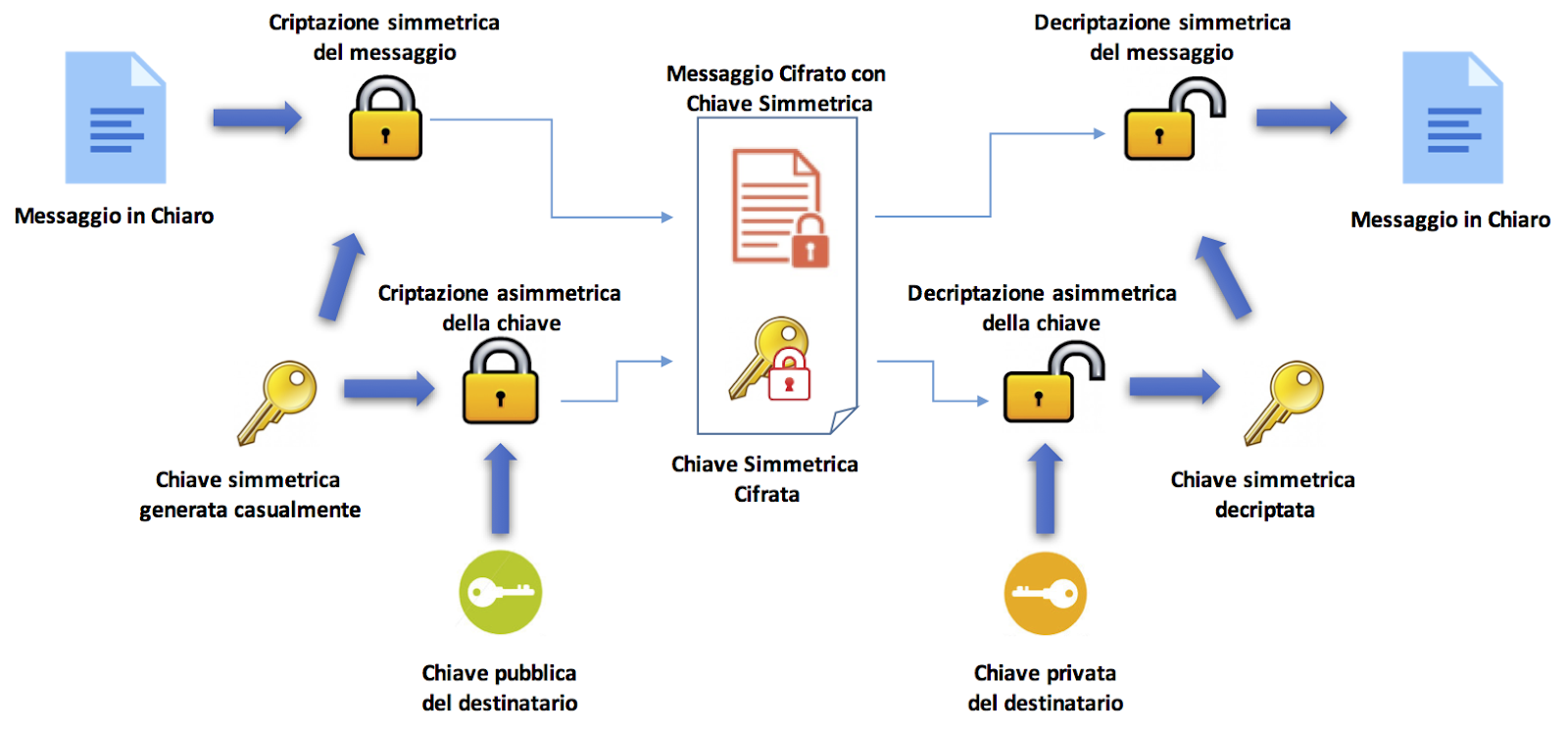
That symmetric refers to a type of text encryption that uses a single key to encrypt and decrypt information:
The encryption key is shared between sender and recipient and is usually agreed upon in advance: it represents the central element that allows users in cryptocurrencies to access and manage their digital resources.
Symmetric encryption with a single key is one of the most common ways to protect passwords, transactions, and communications between operating nodes.
For example, when you transfer money from one wallet to another, it ensures that the information is only read and shared by two parties involved in the transactionwhich protects the data from prying eyes.
However, despite the benefits it brings, symmetric encryption has limitations in terms of scalability and key management.
The need for paired communication significantly limits the extension of this practice in a system with many more users. At the same time, more and more users imply human error in the management and maintenance of the so-called “private key”which if lost results in the loss of crypto or data stored in the virtual wallet.
To overcome these limitations, asymmetric cryptography comes to our rescue by providing a pair of separate keys (public and private) when encrypting and decrypting passwords.
This extra level of security immediately increases data protection: the public key can be shared with anyone on any network (such as when we share our address to receive a payment in crypto), while the private key must be kept secret.
Both keys are generated by an algorithm that uses large prime numbers to create two unique and mathematically linked keys.
Anyway, whoever has the public key can encrypt a message, but only the holder of the private counterpart can decrypt the text. We can imagine this as if it were an email inbox: whoever owns the public key can send a message, but only the owner of the private key can open the email and read the messages.
Non-custodial software wallets such as Trust Wallet or MetaMask use asymmetric cryptography to provide their users with the highest possible security.
Source: https://www.javaboss.it/crittografia-in-java/
The most common formats of encrypted passwords
Password encryption in the crypto and blockchain sector is done according to different formats that can be used for different purposes and provide different levels of security:
- MD5 (message summary 5):
The MD5 algorithm, developed by Ronald Rivest in 1991, generates a 128-bit hash (32 hexadecimal characters) from a variable-length input.
It is no longer considered secure due to vulnerabilities discovered in the algorithm. However, it is still used in some older contexts, for example to verify the integrity of files.
- SHA-1 (Secure Hash Algorithm 1):
SHA-1 generates a 160-bit hash (40 hexadecimal characters).
It is no longer considered as secure as it once was, as it has shown several vulnerabilities: it is now generally being replaced by more robust algorithms such as SHA-256 and SHA-3. However, it continues to be used in a wide range of systems and new applications.
- Salty:
The salt is a random sequence of bits that is added to the password before the hash is calculated.
It solves the problem of collisions (two different passwords generating the same hash) in hash methods.
By adding a salt, even identical passwords will have completely different hashes. This makes it more difficult for attackers to decrypt passwords via brute force attacks.
- Bcrypt:
Bcrypt is a hash algorithm specifically designed for password encryption.
Use a salt and a number of iterations to slow down the hash calculation. It is widely used to protect user passwords in the field of databases.
The choice of encryption format depends on the specific needs of the reference system. Nowadays it is advisable to use hash algorithms such as bcrypt or SHA-2 to protect passwords and limit cyber attacks.
Hash functions and digital signatures
Another way to protect passwords and valuable information in cryptocurrencies is to rely on hash functionswhich are algorithms that transform any form of data into a fixed-length string of characters.
By using robust hashing algorithms, we can effectively protect sensitive information and prevent cyber-attacks.
Hash functions are irreversible: It is not possible to convert a hash back to the original data. They are essential in data management on the blockchain as they allow structuring information without compromising its initial integrity
Hashes can also act as fingerprints for all encrypted passwords, protecting the user from unauthorized actions on their account.
After all, any change to the original data would result in a new hash, which would no longer correspond to the original source and would therefore not be verifiable on the blockchain.
Another method to ensure password security, and more specifically the authenticity and integrity of data contained in a message, is to use the so-called “Digital signatures” (asymmetric cryptography technique).
This is simply a method of ensuring that the owner of that specific data approves the transaction. Generally, the sender creates the digital signature using a private key to encrypt the signature data, while the recipient obtains the signer’s public key to decrypt the data. This code provides irrefutable proof that a message was created solely by the sender and has not been tampered with online.
When we talk about digital signatures, we immediately think of signature devices such as Ledger, Trezor and Bitbox that allow a transaction to be validated before it is broadcast to the rest of a cryptographic network.
However, make sure you don’t think of these devices as wallets: they do not hold your cryptocurrencies, but only allow you to authorize the transactions necessary to spend them.
We often say: “my crypto is ON my Ledger”.
But your digital assets aren’t actually physically stored on your Ledger; they are on the blockchain.
Your Ledger stores and protects your private keys and keeps them safe so you can fully own and control your assets.@iancr explains: pic.twitter.com/PGrmQIvKpV
— Ledger (@Ledger) May 11, 2023

